Conceptual Business Illustration Words Trusted Computing Stock Illustration 1015010017 | Shutterstock

CISSP PRACTICE QUESTIONS – 20210125 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Wibu-Systems joins the Trusted Computing Group to leverage Trusted Platform Modules as secure licensing elements: Wibu-Systems




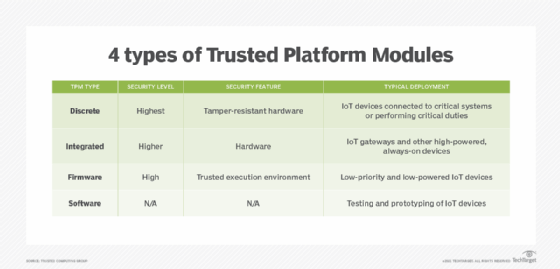

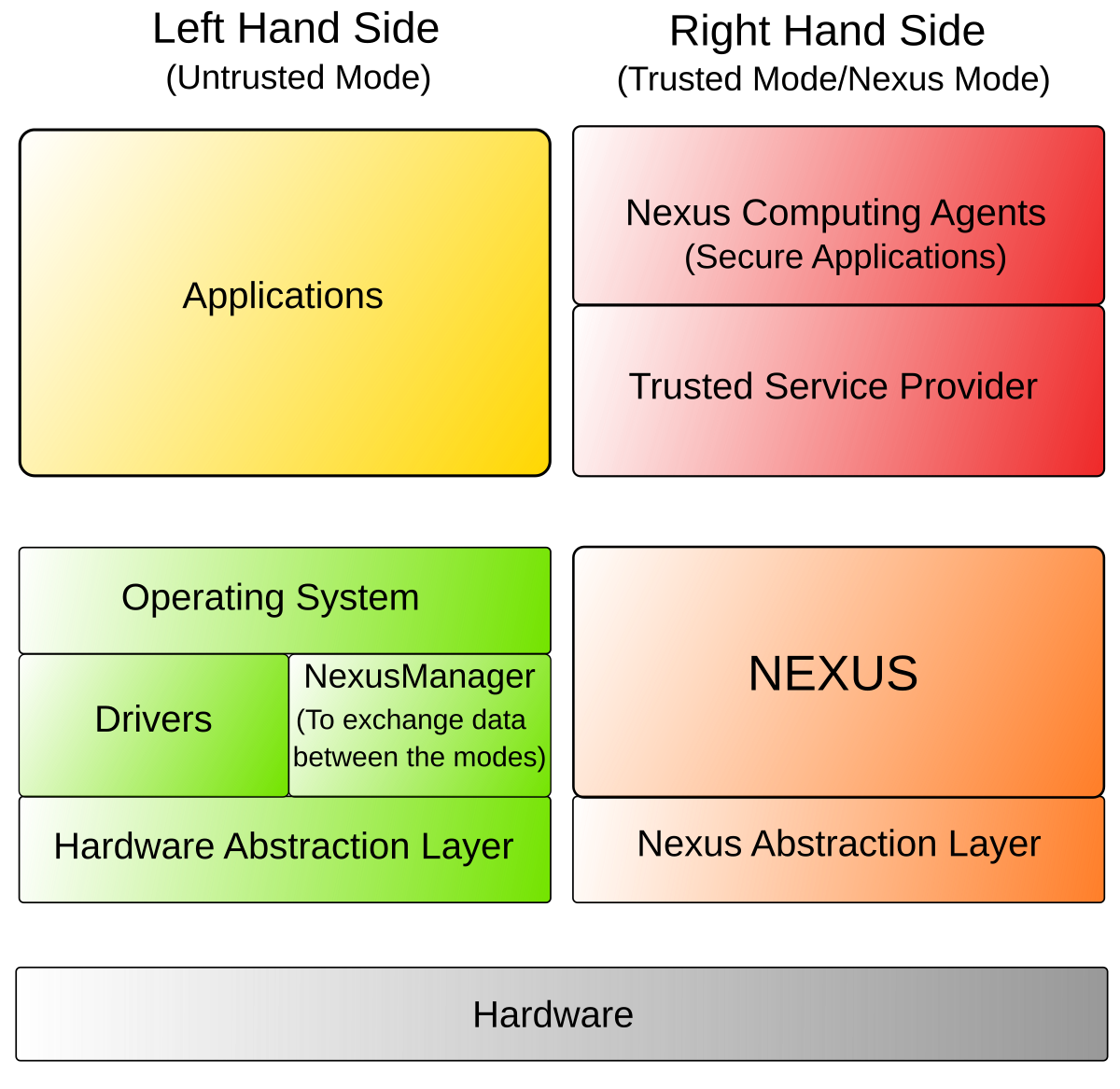





![PDF] Trusted Computing Platforms , the Next Security Solution | Semantic Scholar PDF] Trusted Computing Platforms , the Next Security Solution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4a82f9c66e39b1335bdc8fa3eb0880e9a0370446/12-Figure5-1.png)