How to exploit Active Directory remotely by using MSBuild + Metasploit + Bloodhound – Cyber Security Corner

Post-Exploitation Basics In Active Directory Environment By Hashar Mujahid | by Hashar Mujahid | Aug, 2022 | InfoSec Write-ups
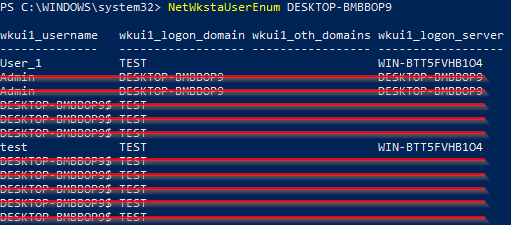
BloodHound Inner Workings & Limitations – Part 2: Session Enumeration Through NetWkstaUserEnum & NetSessionEnum – Compass Security Blog