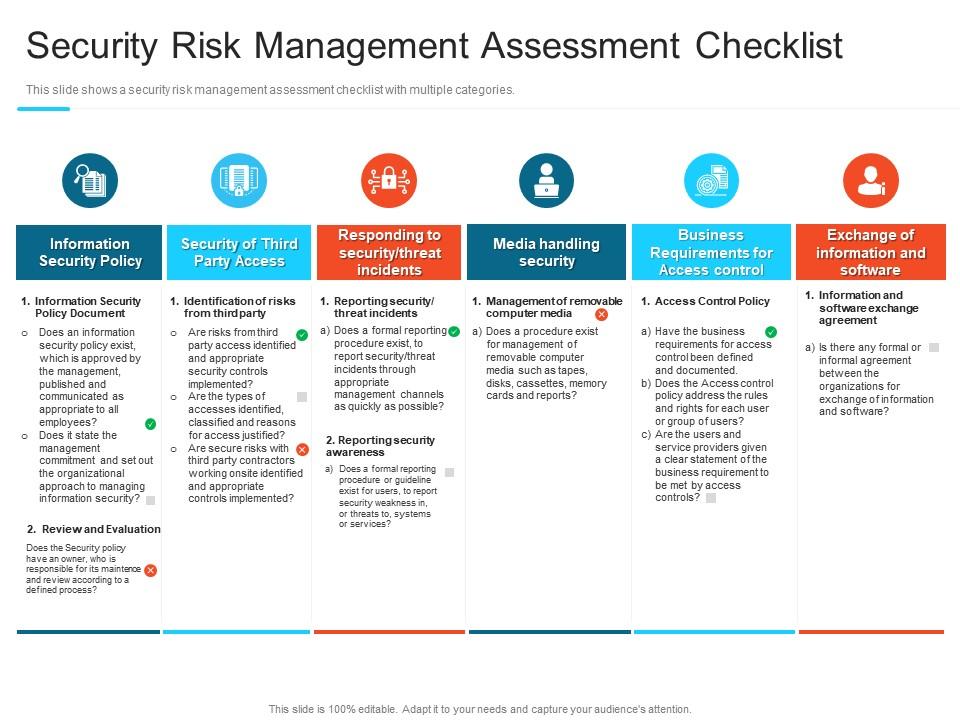
Security Risk Management Assessment Checklist Steps Set Up Advanced Security Management Plan | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
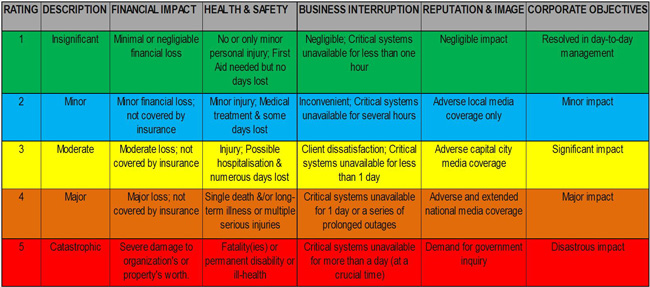
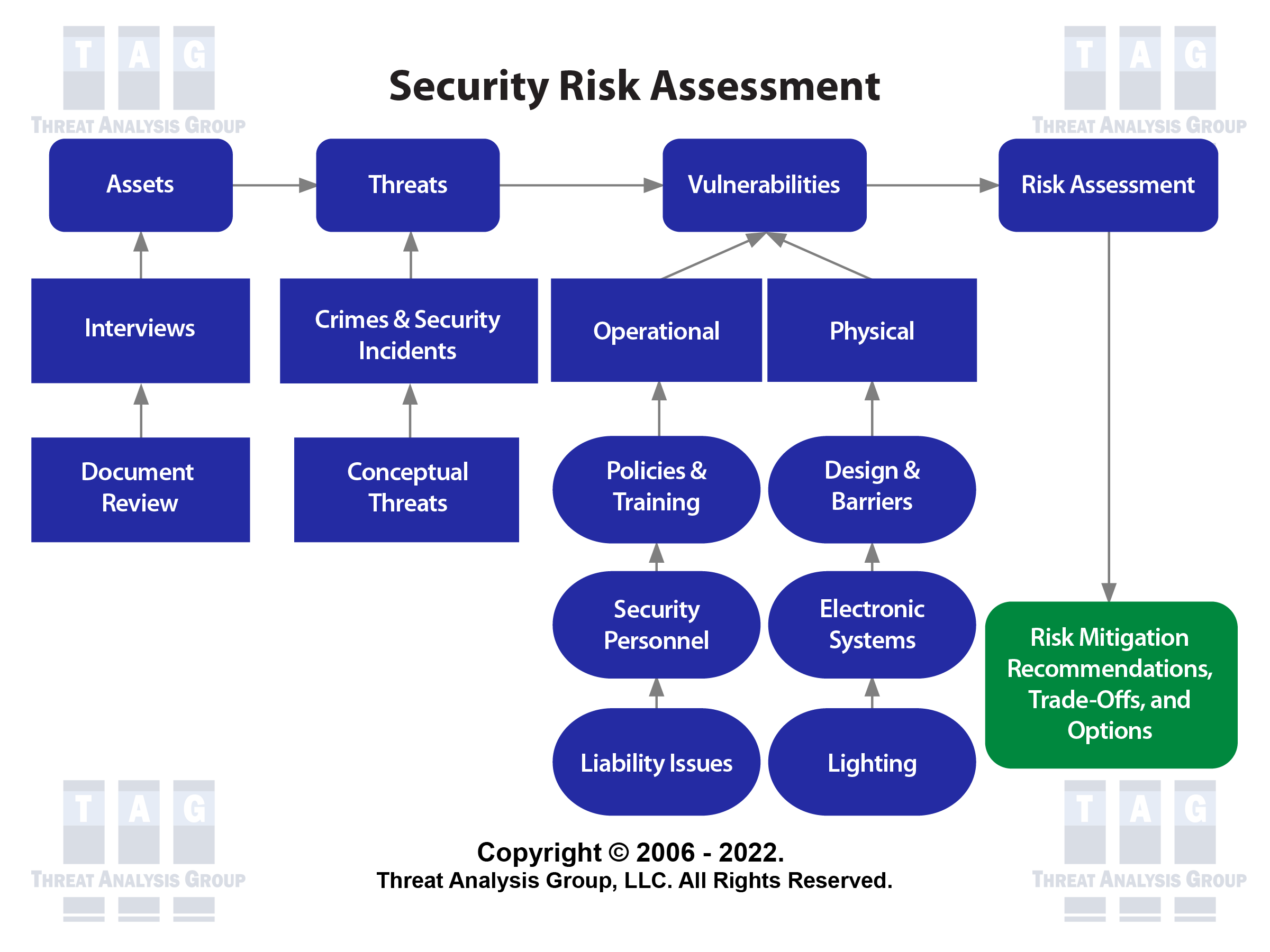
Security Risk Assessment Shows Where Security Dollars Are Best Spent - Facilities Management Insights

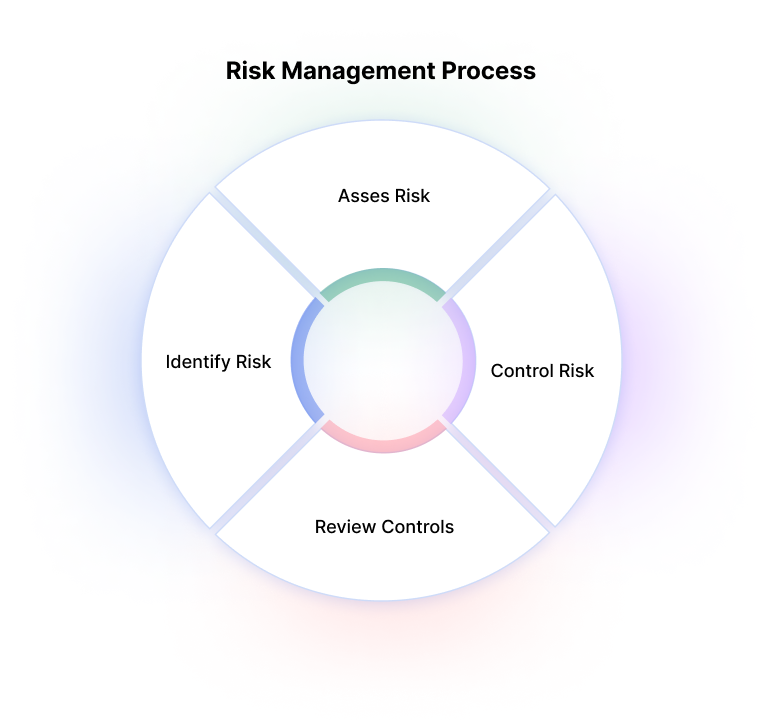

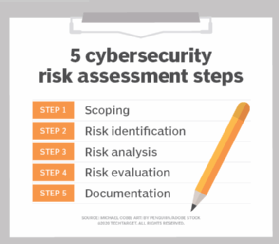



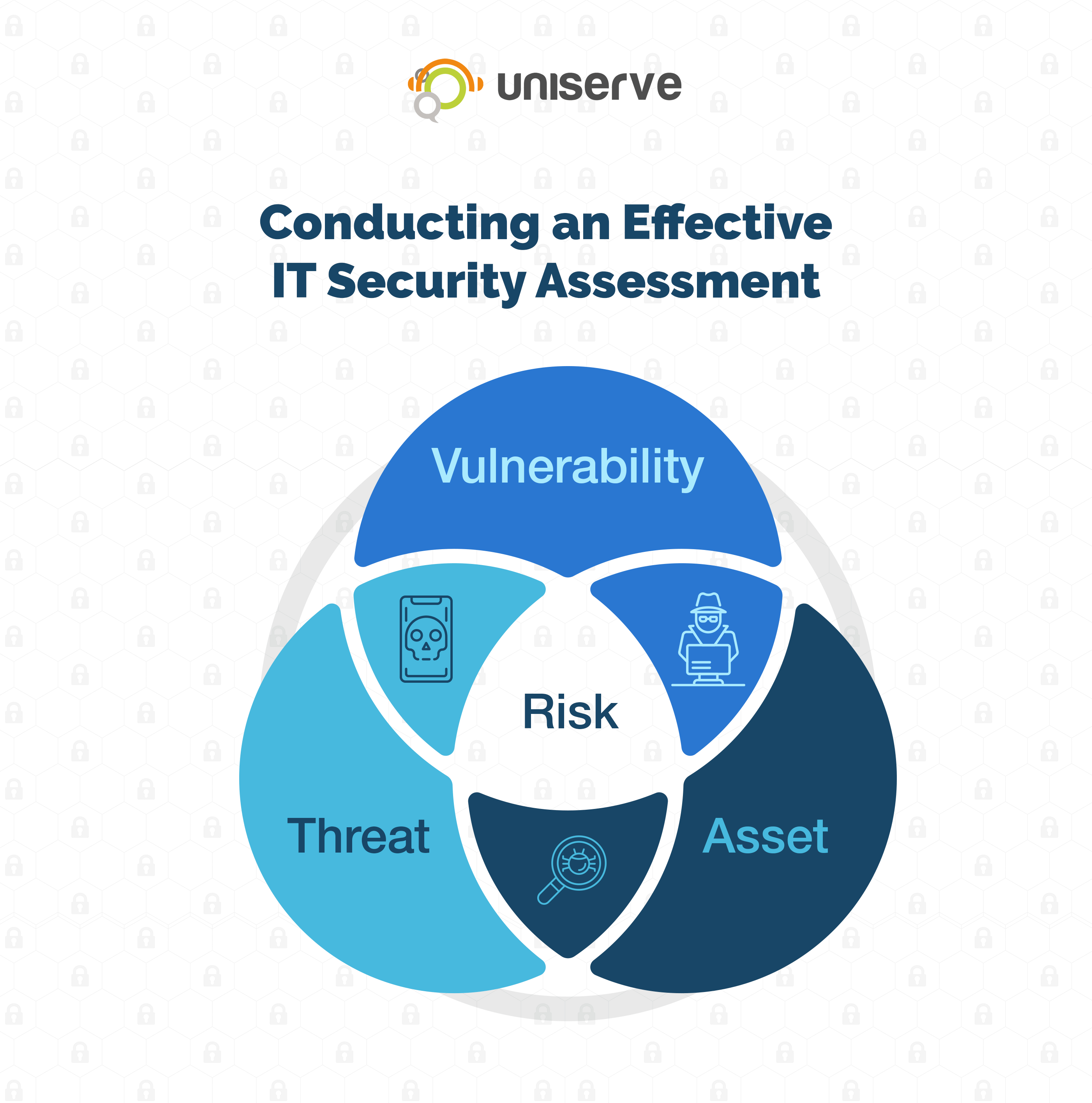


![Security+: risk management processes and concepts [updated 2021] - Infosec Resources Security+: risk management processes and concepts [updated 2021] - Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/Table2.png)