An architectural Overview of Information Security Management System for... | Download Scientific Diagram
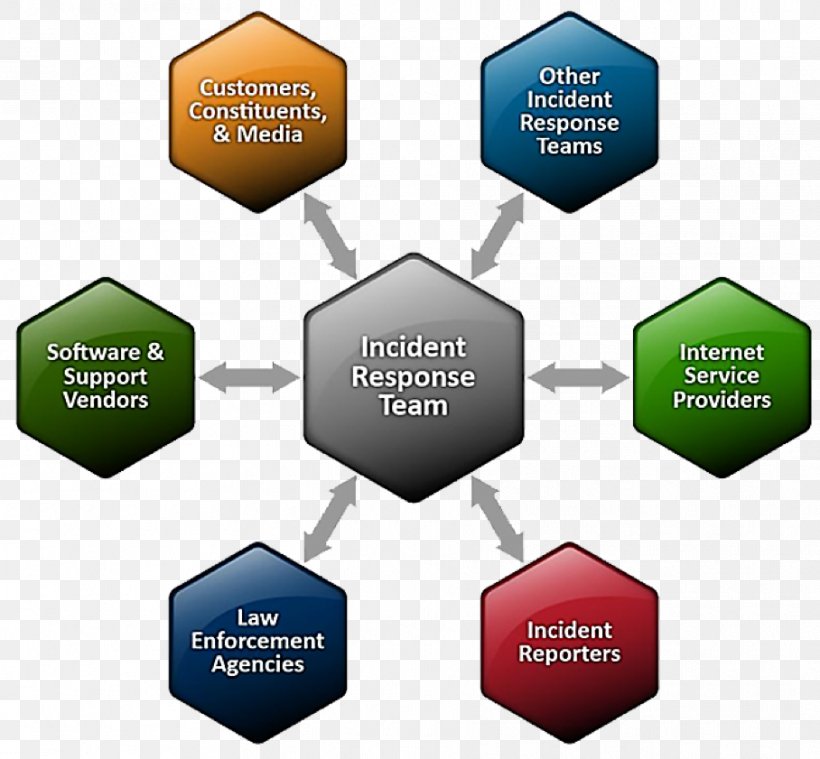
Computer Security Incident Management Incident Response Team Computer Emergency Response Team, PNG, 908x841px, Incident Management, Brand,
![How Can I Get an Entry-Level Cybersecurity Job? [Guide] How Can I Get an Entry-Level Cybersecurity Job? [Guide]](https://onlinedegrees.sandiego.edu/wp-content/uploads/2020/08/USD-Cyber-Entry-Level-Job-Career-Guide-1-1-1.jpeg)

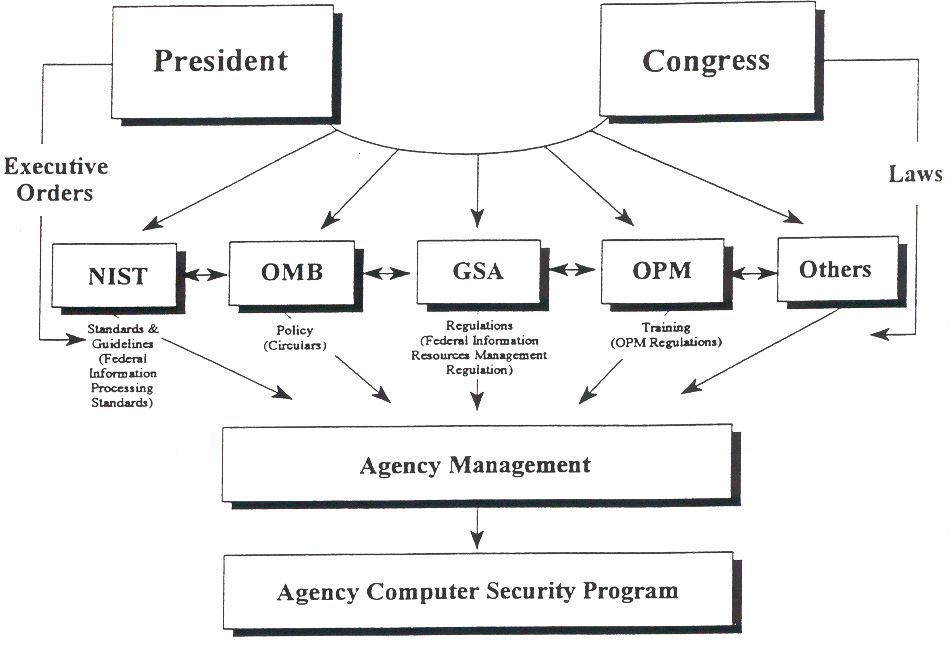
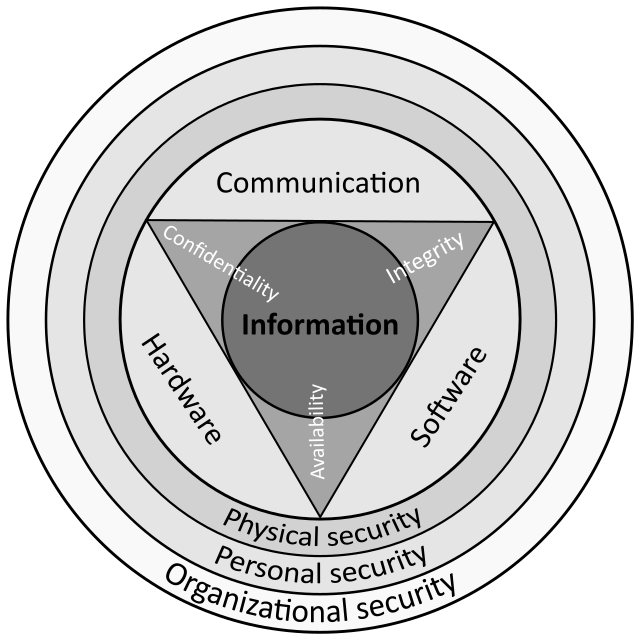







![PDF] Data Security Management in Distributed Computer Systems | Semantic Scholar PDF] Data Security Management in Distributed Computer Systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e50273c9b438a02db5d1376d549f2f539189fbee/8-Figure5-1.png)








