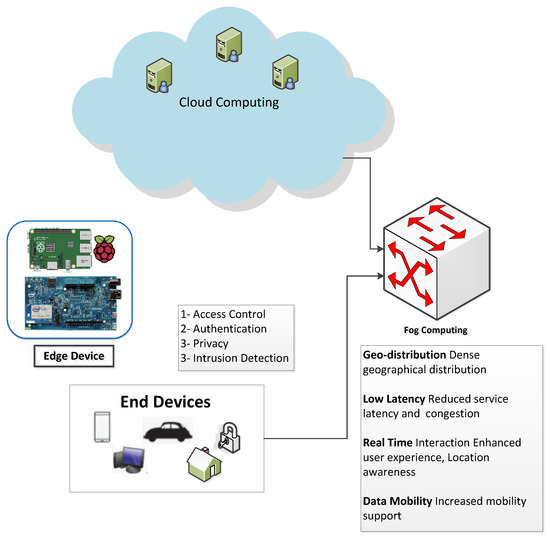
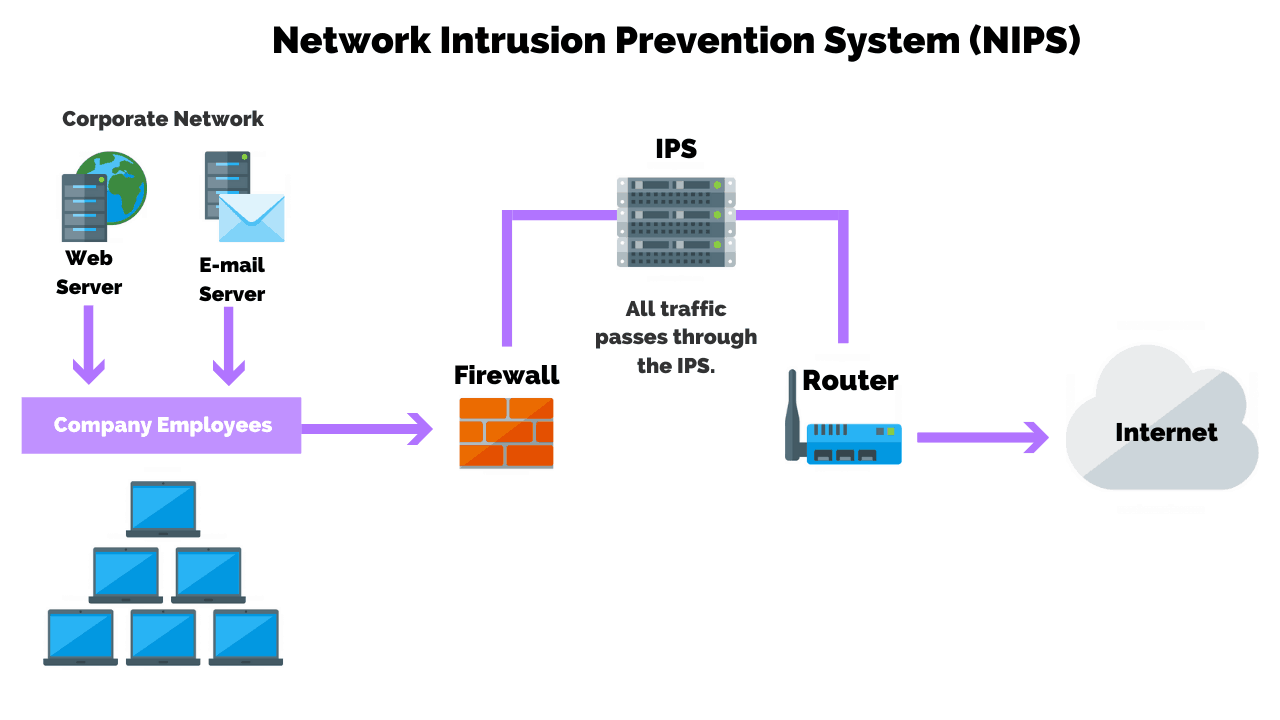
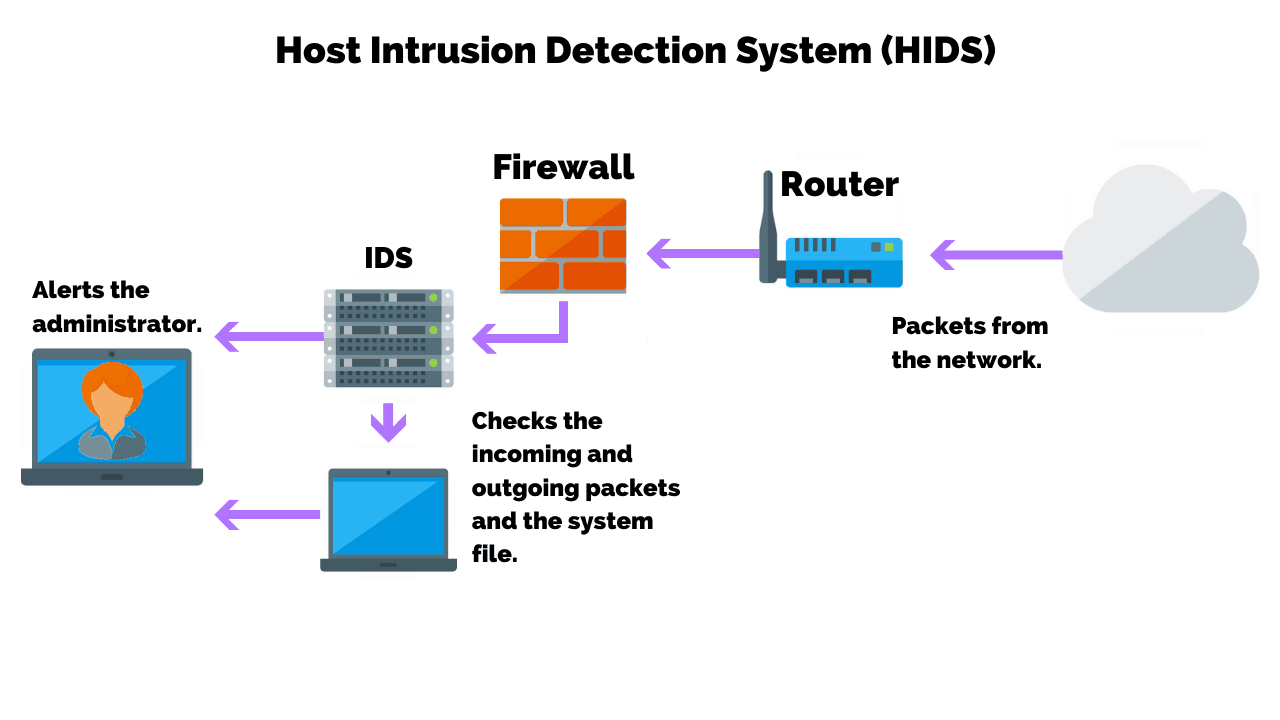
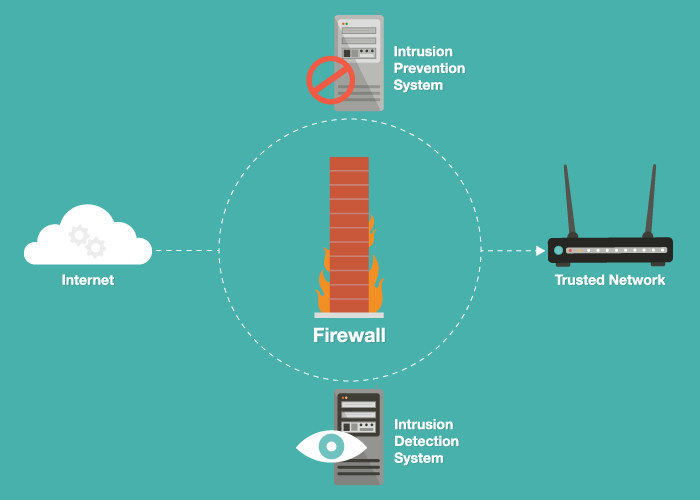
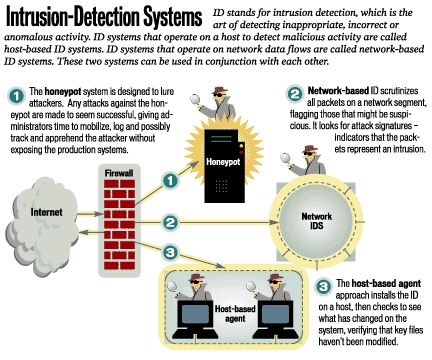
Computational intelligence intrusion detection techniques in mobile cloud computing environments: Review, taxonomy, and open research issues - ScienceDirect

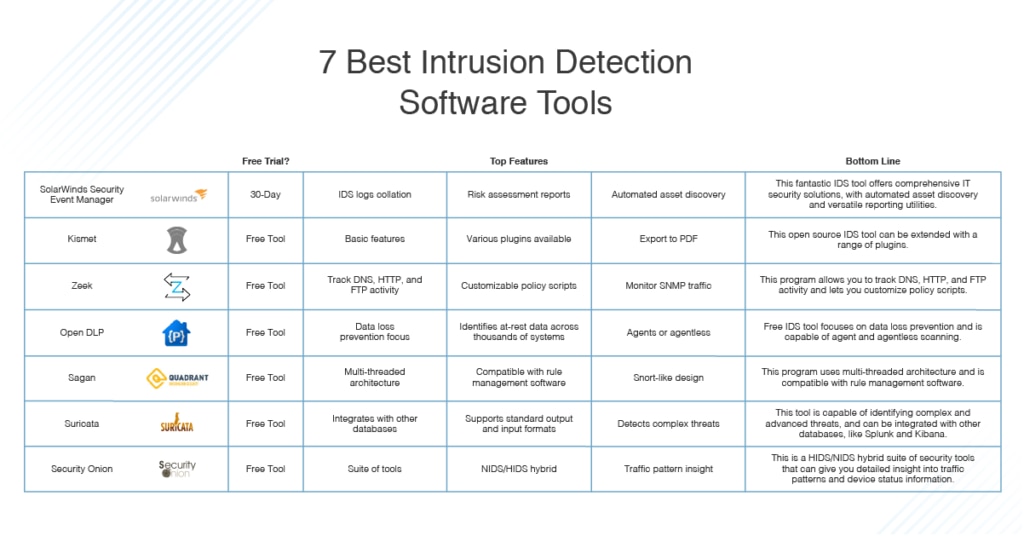
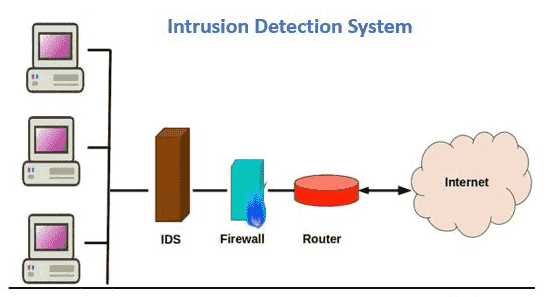
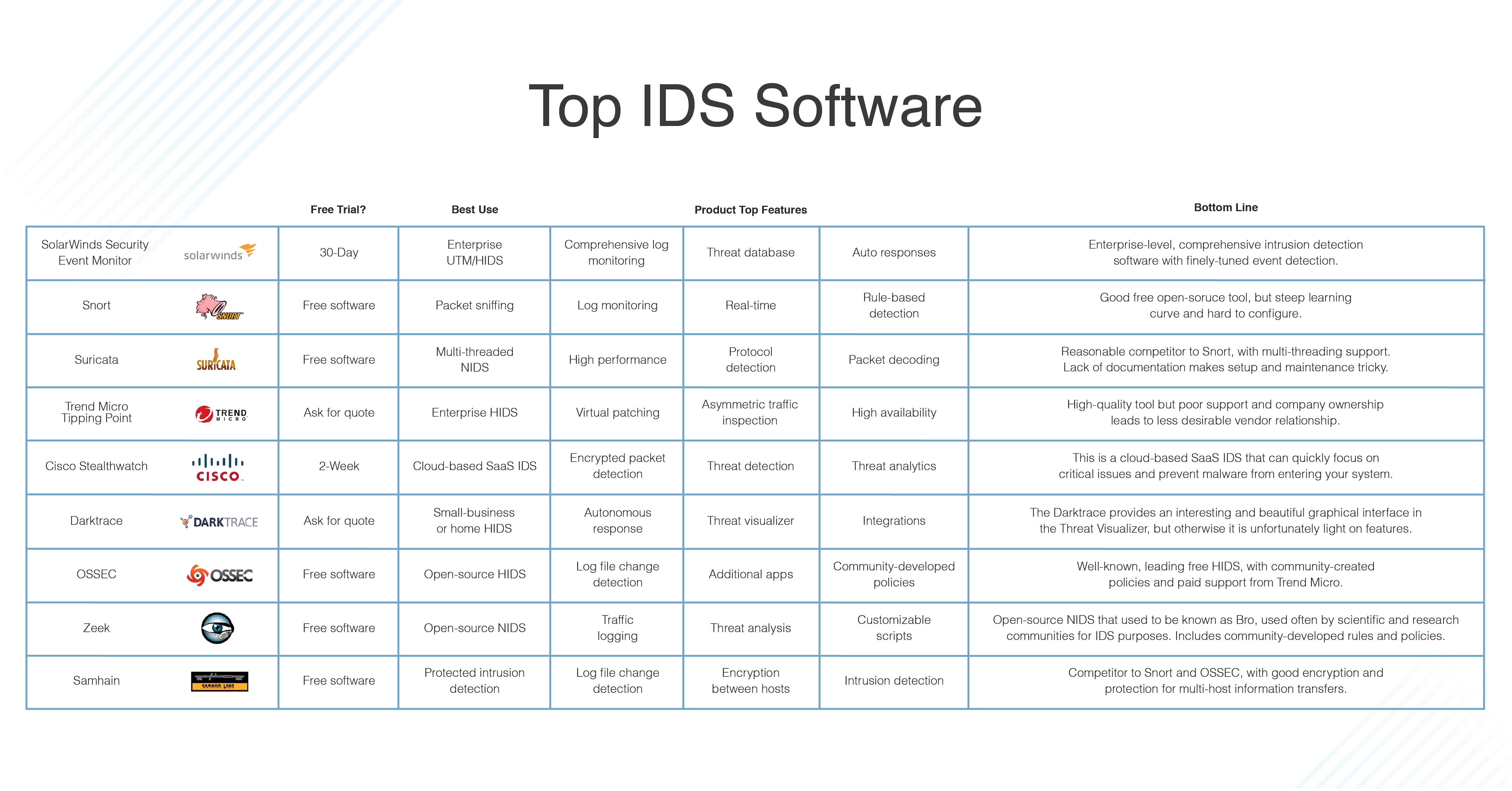
Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Vindicator Intrusion Detection System (IDS) | Intrusion Detection Systems (IDS) | Vindicator Technologies | Integrated Security | Honeywell Commercial Security

Intrusion Detection Honeypots: Detection through Deception: Sanders, Chris: 9781735188300: Books - Amazon

Computer Intrusion Detection and Network Monitoring: A Statistical Viewpoint (Information Science and Statistics): Marchette, David J.: 9780387952819: Books - Amazon