How to hack into mobile phones via bluetooth & How to Hack Wireless Internet Connections in 3 Easy Steps PresentedBy Pradosh H.S. - ppt download
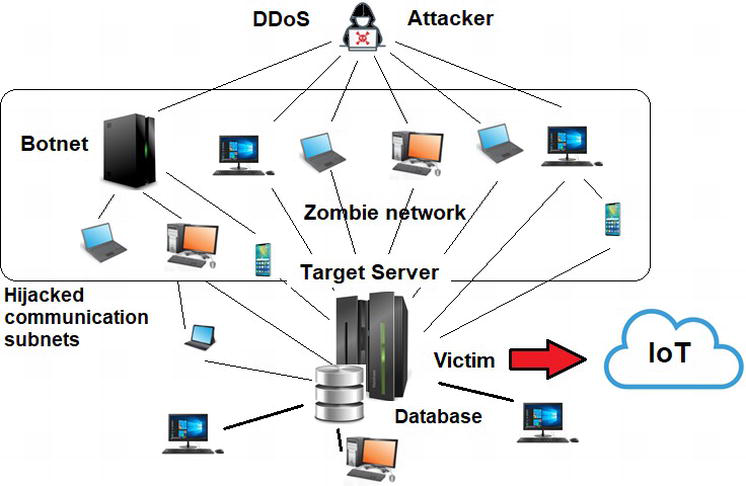
Internet of Things and Distributed Denial of Service as Risk Factors in Information Security | IntechOpen
SECURITY Question] DOS Attack / data flooding on bluetooth layer possible? · Issue #309 · corona-warn-app/cwa-documentation · GitHub
![PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9f8a42ec37bb11cbef56b6dad90c5b249a3f20ac/5-Figure13-1.png)
PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar




![What is a DoS Attack and How to DoS Someone [Ping of Death] What is a DoS Attack and How to DoS Someone [Ping of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks3.png)